[et_pb_section bb_built=”1″ fullwidth=”on” _builder_version=”3.11″ next_background_color=”#000000″][et_pb_fullwidth_image src=”https://alpharecon.com/wp-content/uploads/2018/09/alpha-recon-pro-web-mobile-screenshot-school-security-THREE-FACTORS-TO-CONSIDER-WHEN-CHOOSING-A-RISK-INTELLIGENCE-PROGRAM-FOR-YOUR-SCHOOL.jpg” disabled_on=”on|off|” _builder_version=”3.11″ max_width=”50%” module_alignment=”center” custom_margin=”|||” custom_padding=”|||”]
[/et_pb_fullwidth_image][et_pb_fullwidth_post_title date=”off” featured_image=”off” text_background=”on” text_bg_color=”rgba(255,255,255,0.65)” disabled_on=”on|off|off” _builder_version=”3.11″ title_font=”|||on|||||” title_text_color=”#005106″ title_font_size=”35px” title_font_size_tablet=”30px” title_font_size_phone=”25px” title_font_size_last_edited=”on|phone” title_line_height=”1.2em” title_line_height_last_edited=”on|phone” meta_text_color=”#666666″ meta_line_height=”3em” meta_line_height_last_edited=”on|desktop” text_orientation=”center” custom_margin=”|||” custom_padding=”0px|||” custom_padding_last_edited=”off|desktop” custom_css_post_title=”padding-right: 20px;||padding-left: 20px;”]
[/et_pb_fullwidth_post_title][et_pb_fullwidth_post_title date=”off” featured_placement=”above” text_background=”on” text_bg_color=”rgba(255,255,255,0.65)” disabled_on=”off|on|on” _builder_version=”3.11″ title_font=”|||on|||||” title_text_color=”#005106″ title_font_size=”35px” title_font_size_tablet=”30px” title_font_size_phone=”25px” title_font_size_last_edited=”on|phone” title_line_height=”1.2em” title_line_height_last_edited=”on|phone” meta_text_color=”#666666″ meta_line_height=”3em” meta_line_height_last_edited=”on|desktop” background_color=”#ffffff” background_size=”contain” text_orientation=”center” custom_margin=”|||” custom_padding=”|||” custom_padding_last_edited=”off|desktop” custom_css_post_title=”padding-top: 20px;||padding-right: 20px;||padding-left: 20px;”]
[/et_pb_fullwidth_post_title][/et_pb_section][et_pb_section bb_built=”1″ make_fullwidth=”on” use_custom_gutter=”on” gutter_width=”2″ specialty=”on” _builder_version=”3.11″ custom_padding=”|20px||20px||true” prev_background_color=”#000000″][et_pb_column type=”3_4″ specialty_columns=”3″][et_pb_row_inner admin_label=”Row” _builder_version=”3.0.47″][et_pb_column_inner type=”4_4″ saved_specialty_column_type=”3_4″][et_pb_text admin_label=”Paragraph” _builder_version=”3.11″ text_font_size=”15px”]
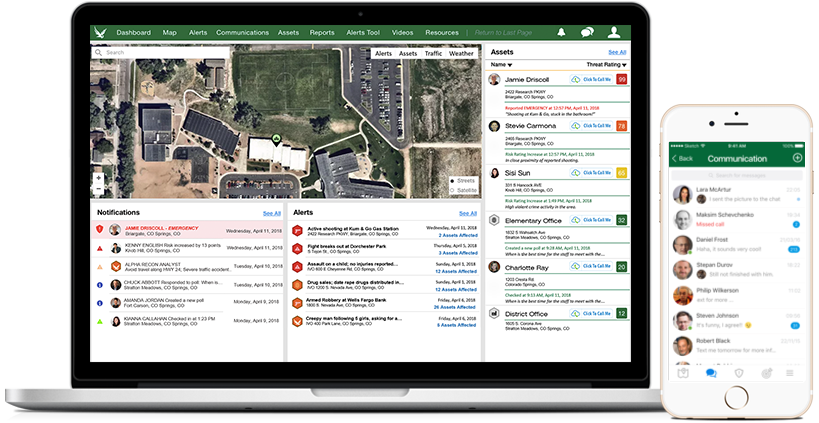
There is a lot of press and attention being paid to school safety and security. Although the data suggests there is an extremely low probability of a school shooting on campus, recent tragedies have alerted administrations of the need for effective risk management programs and quality intelligence. It has also opened up and provided a greater opportunity for risk managers.
Several vendors have answered the call to provide safety and security services due to the perceived business opportunity. However, it is unfair and borderline manipulative to offer ineffective solutions to organizations that have little knowledge of intelligence operations or the proper way to assess them. Organizations can waster tens-of-thousands of dollars on overhyped and ineffective solutions that rarely deliver as promised.
Alpha Recon will be hosting a series of webinars and delivering content to help prospective buyers understand what to look for and how to differentiate hype and actual value. Based on our core belief in enterprise security risk management, our holistic, comprehensive, and intelligent centered approach focuses on key organizational goals and assets. Alpha Recon will be advising the education industry on optimal risk and security management programs and how intelligence must be at the center of a well-rounded solution. If you are attending this year’s ASIS convention in Las Vegas, we invite you to visit us and we will be happy to help your organization make an inform decision.
Here are three important areas that schools must focus on when choosing a risk intelligence solution:
[/et_pb_text][/et_pb_column_inner][/et_pb_row_inner][et_pb_row_inner _builder_version=”3.11″][et_pb_column_inner type=”1_2″ saved_specialty_column_type=”3_4″][et_pb_text admin_label=”Header 1″ _builder_version=”3.11″ header_2_font=”|600|||||||” header_2_text_color=”#005106″]
1. Access and Redundancy of Threat Data
[/et_pb_text][et_pb_text admin_label=”Paragraph 1″ _builder_version=”3.11″ text_font_size=”15px”]
There are several providers that have serious limitations of data acquisition. Many will rely on only one or two data sources (usually social media) that do not provide a complete risk profile. Given the recent privacy controls, vendors that rely mainly on social media will not offer effective intelligence and will mostly be a waste of money. These providers will lock you into an annual contract with a false sense of security. Do not enter into any service contract until you have tried the service for yourself, and have observed relevant threat intelligence.
[/et_pb_text][/et_pb_column_inner][et_pb_column_inner type=”1_2″ saved_specialty_column_type=”3_4″][et_pb_text admin_label=”CTT” _builder_version=”3.11″ text_font_size=”20px” text_line_height=”1.8em” border_width_top=”1px” border_color_top=”#d8d8d8″ border_width_bottom=”1px” border_color_bottom=”#d8d8d8″ custom_margin=”|||” custom_padding=”||20px|” filter_saturate=”0%”]
“Given the recent privacy controls, vendors that rely mainly on social media will not offer effective intelligence and will mostly be a waste of money.”
@alphareconpro
[/et_pb_text][/et_pb_column_inner][/et_pb_row_inner][et_pb_row_inner custom_padding=”0|0px|0|0|false|false” _builder_version=”3.11″][et_pb_column_inner type=”4_4″ saved_specialty_column_type=”3_4″][et_pb_image src=”https://alpharecon.com/wp-content/uploads/2018/09/school-safety-security-esrm-alpha-recon-risk-management-erm-mid.jpg” align=”center” _builder_version=”3.11″]
[/et_pb_image][/et_pb_column_inner][/et_pb_row_inner][et_pb_row_inner admin_label=”Row” _builder_version=”3.0.47″][et_pb_column_inner type=”4_4″ saved_specialty_column_type=”3_4″][et_pb_text admin_label=”Paragraph 1 (continued full width)” _builder_version=”3.11″ header_2_font=”|600|||||||” header_2_text_color=”#005106″]
Look at vendors who, directly or through partnerships, will provide multiple sources of data that include social media, targeted open source web data, blogs, deep web, dark web (as appropriate), crowd-sourced data, and the opportunity to ingest internal data. Paying tens-of-thousands of dollars per year for limited Twitter and Facebook data is not cost effective and will rarely yield the results you deserve. Many students are moving away form these social media channels, and privacy concerns will make these collections extremely difficult.
A good intelligence capability will use cutting edge data technology, tap into multiple and redundant sources, and provide quality content and noise-controlled intelligence to your organization. School districts and states should not use an RFP (request for proposal) type process to find vendors as these will skip any pilot or test programs. The RFP process allows for dishonesty and never allows for a trial process before making a decision. Using the software is paramount to ascertaining real value. Don’t believe the sales pitches. Ask intelligent questions about where companies get their data, how they process information, and what will happen when Twitter and Facebook shut off or limits their access. These are dark secrets they aren’t willing to share with you up front.
[/et_pb_text][/et_pb_column_inner][/et_pb_row_inner][et_pb_row_inner admin_label=”Row” _builder_version=”3.0.47″][et_pb_column_inner type=”4_4″ saved_specialty_column_type=”3_4″][et_pb_text admin_label=”Header 2″ _builder_version=”3.11″ header_2_font=”|600|||||||” header_2_text_color=”#005106″]
2. Timeliness of Intelligence and Realistic Expectations
[/et_pb_text][et_pb_text admin_label=”Paragraph 2″ _builder_version=”3.11″ text_font_size=”15px”]
In several spec-ops deployments, we relied on robust intelligence networks to inform our operation and help us meet requirements. Getting the right intelligence at the right time was critical in saving countless lives. This is equally applicable when protecting your school operations and campuses. How fast does a vendor get their information, what technology processes are used, and how quickly does intelligence get to the decision maker? What vehicles deliver the intelligence and in what format? How quickly can intelligence be used?
Many vendors promise that will get you the information yo need within minutes. There will even be hand-picked case studies that look at the time they received a tweet 7 minutes before the media did. This is exciting, right? Look more closely. Usually the events schools care about won’t necessarily be on the news and aren’t being monitored by these vendors.
Furthermore, the number of incidents missed will far outweigh the events captured promptly. Vendors will not broadcast these statistics. It is more meaningful to look at metrics such as “school relevant threat events detected,” and “a ratio of threat events collected vs. not collected,” or an average time of delivery to the client across all threat categories. It’s easy to highlight the few times you got the information right and delivered it quickly, but how often will this happen and how valuable is the information that these vendors think is important to you?
Some competent intelligence enterprises leverage technology that will be straightforward and honest about what they can and cannot do. But many more will not. It is up to you to ask the right questions about speed and deliver of intelligence across all threat types and sources. Human-derived and analyzed intelligence is slower and more expensive, while technology enabled intelligence is faster but subject to error and relative performance. Make sure yo know what quality control measures are in place, where a human provides curation, and how this impacts the speed of intelligence delivery.
[/et_pb_text][/et_pb_column_inner][/et_pb_row_inner][et_pb_row_inner _builder_version=”3.11″][et_pb_column_inner type=”1_2″ saved_specialty_column_type=”3_4″][et_pb_text admin_label=”Header 3″ _builder_version=”3.11″ header_2_font=”|600|||||||” header_2_text_color=”#005106″]
3. Relevance and “Information vs Intelligence”
[/et_pb_text][et_pb_text admin_label=”Paragraph 3″ _builder_version=”3.11″ text_font_size=”15px”]
It is worthwhile to point out the difference between information and intelligence. Raw data information is useless and can be detrimental to operations without it being related and analyzed according to organizational assets, requirements, and operational plans. Many “data-as-a-service” companies are going out of business because client’s don’t have the time, resources, technology, or subject matter expertise to leverage information.
[/et_pb_text][/et_pb_column_inner][et_pb_column_inner type=”1_2″ saved_specialty_column_type=”3_4″][et_pb_text admin_label=”CTT” _builder_version=”3.11″ text_font_size=”20px” text_line_height=”1.8em” border_width_top=”1px” border_color_top=”#d8d8d8″ border_width_bottom=”1px” border_color_bottom=”#d8d8d8″ custom_margin=”|||” custom_padding=”||20px|” filter_saturate=”0%”]
“Intelligence is aggregated, processed, and finished information that relates to your requirements, assets, and goals while helping you make important decisions.”
@alphareconpro
[/et_pb_text][/et_pb_column_inner][/et_pb_row_inner][et_pb_row_inner custom_padding=”0|0px|0|0|false|false” _builder_version=”3.11″][et_pb_column_inner type=”4_4″ saved_specialty_column_type=”3_4″][et_pb_image src=”https://alpharecon.com/wp-content/uploads/2018/09/social-media-facebook-twitter-privacy-data-esrm-risk-management-alpha-recon-school-security-mid.jpg” align=”center” _builder_version=”3.11″]
[/et_pb_image][/et_pb_column_inner][/et_pb_row_inner][et_pb_row_inner admin_label=”Row” _builder_version=”3.0.47″][et_pb_column_inner type=”4_4″ saved_specialty_column_type=”3_4″][et_pb_text admin_label=”Paragraph 3 (continued full width)” _builder_version=”3.11″ header_2_font=”|600|||||||” header_2_text_color=”#005106″]
“Noise” in data science and intelligence is a problematic factor, and it data is not made relevant to what you care about (your assets), it just takes up your valuable time and energy to sift evaluate.
Intelligence is aggregated, processed, and finished information that relates to your requirements, assets, and goals while helping you make important decisions. These decisions can be based on immediate threats or trends that require a watchful eye.
Many vendors will provide unfinished information or alerts that don’t relate to what’s important. We call it threat spamming and in some cases the information has not been carefully analyzed by technology or analysts. There are very few vendors that provide finished intelligence that relates to your organization and their assets. Is it enough to get a series of general alerts delivered in an email or SMS message, or do you need context and reporting that explores emerging and current threats more deeply? Intelligence should aid and improve decision making success. It should also work to improve defined outcomes and monitor key risks and vulnerabilities facing your organization. If you are receiving just “information,” you are likely going to spend more time trying to understand it than leveraging it. This makes it less valuable, and in many cases distracting.
Ask vendors to explain the difference between their “information” and “intelligence” and how and what they do to offer true, meaningful intelligence. Also ask them about delivery, context, and reporting capabilities. What algorithms are involved in developing this intelligence? Is ti based on machine learning or merely keyword lists? What formats will you receive and be able to access this intelligence? Is it easy to use and understand? Is the intelligence relevant? Can you shape the collection principles? Can you change the delivery of alerts and viewing of geospatial intelligence? Is the risk intelligence related to your assets? How is that done and how can you utilize it to better protect and manage what matters most? How does it support a risk culture?
[/et_pb_text][/et_pb_column_inner][/et_pb_row_inner][et_pb_row_inner admin_label=”Row” _builder_version=”3.0.47″][et_pb_column_inner type=”4_4″ saved_specialty_column_type=”3_4″][et_pb_divider color=”#d8d8d8″ _builder_version=”3.11″ max_width=”50%” module_alignment=”center”]
[/et_pb_divider][et_pb_text admin_label=”Ending, Contact” _builder_version=”3.11″ text_font_size=”15px”]
We hope you found this useful and helpful to elevate the importance of effective risk intelligence platforms for your schools and campuses. At a minimum, this should stimulate thought and and discussion on this important topic. We at Alpha Recon are passionate about risk management for schools and the education industry. If we can be of any help, don’t hesitate to reach out to us to see how your school can benefit from the most advanced security risk management solution on the market!
[/et_pb_text][/et_pb_column_inner][/et_pb_row_inner][et_pb_row_inner _builder_version=”3.11″][et_pb_column_inner type=”1_2″ saved_specialty_column_type=”3_4″][et_pb_button button_url=”/demo” button_text=”Schedule a Demo” button_alignment=”center” _builder_version=”3.11″ custom_button=”on” button_text_color=”#ffffff” button_bg_color=”#f56600″ button_border_color=”#f56600″ button_icon=”%%116%%” button_icon_placement=”left”]
[/et_pb_button][/et_pb_column_inner][et_pb_column_inner type=”1_2″ saved_specialty_column_type=”3_4″][et_pb_button button_url=”/contact” button_text=”Contact Us” button_alignment=”center” _builder_version=”3.11″ custom_button=”on” button_text_color=”#ffffff” button_bg_color=”#f56600″ button_border_color=”#f56600″ button_icon=”%%116%%” button_icon_placement=”left”]
[/et_pb_button][/et_pb_column_inner][/et_pb_row_inner][et_pb_row_inner _builder_version=”3.11″ global_module=”3183″][et_pb_column_inner type=”4_4″ saved_specialty_column_type=”3_4″][et_pb_image global_parent=”3183″ src=”https://alpharecon.com/wp-content/uploads/2018/07/toby.png” align=”center” _builder_version=”3.11″ max_width=”40%” module_alignment=”center” /][et_pb_team_member global_parent=”3183″ name=”Toby Houchens” position=”CEO & Founder” facebook_url=”http://facebook.com/alphareconpro” twitter_url=”http://twitter.com/alphareconpro” linkedin_url=”https://www.linkedin.com/in/tobyhouchens/” icon_color=”#3a3a3a” icon_hover_color=”#005106″ _builder_version=”3.11″ header_font=”||||||||” body_font=”||||||||” text_orientation=”center” max_width_last_edited=”off|desktop” module_alignment=”center”]
Toby is a risktech and ESRM futurist who earned two Master’s degrees in Biology (Neuroscience) and International Relations in addition to becoming a member of the US Army Special Forces, more commonly known as the Green Berets. After leaving the military with over 10 years of risk management and intelligence experience, Toby founded Alpha Recon to be a risk technology innovator in enterprise security risk management (EsRM). Focused on rapidly changing and diverse risk management challenges across traditional corporate boundaries, Toby is a proponent of strategy and intelligence-focused risk management, limiting liabilities while advancing opportunities and outcomes for business with the help of machine learning/AI. Toby is an unconventional thinker who believes that solutions have remained siloed, irrelevant, and rarely lower risk or provide opportunity for organizations and their assets in a measurable and proactive way.
Toby served around the world in high threat areas advising senior military, foreign governments, and U.S. government officials and dignitaries. Engaging with local communities he gained first-hand security and risk management experience in complex environments. During this time, Toby became an expert in risk management, intelligence operations, and threat mitigation with an appreciation for proactive and practical methods. His equal appreciation for deep learning and risk models to synthesize multi-variate data and make it valuable is evident in Alpha Recon’s software approach. Toby’s theories and ideas about holistic risk understanding and strategic management challenge the status quo and will no doubt result in better practices and solutions to help the performance of enterprises around the world. Toby enjoys speaking about innovations in risk technology, measurable risk management, and building consensus for enterprise security risk management around the world
[/et_pb_team_member][/et_pb_column_inner][/et_pb_row_inner][et_pb_row_inner disabled_on=”off|off|off” _builder_version=”3.11″ global_module=”3184″][et_pb_column_inner type=”4_4″ saved_specialty_column_type=”3_4″][et_pb_signup global_parent=”3184″ mailchimp_list=”Alpha Recon|e29af5d16f” mailchimp_account_name=”Alpha Recon” mailchimp_api_key=”889861588abead920c69609029037620-us8″ title=”Alpha Recon Newsletter” description=”<p><img src=%22https://alpharecon.com/wp-content/uploads/2018/02/Travel_Recon_logo.png%22 width=%2277%22 height=%2275%22 alt=%22%22 class=%22wp-image-614 alignnone size-full%22 style=%22display: block; margin-left: auto; margin-right: auto;%22 /></p> <p>The experts at Alpha Recon will be providing more in-depth ERM analysis at upcoming events, in white papers, and webinars. Sign up for our newsletter so you don’t miss out on anything!</p> ” footer_content=”<p><em>Your information is secure and will never be shared.</em></p> ” focus_text_color=”#005106″ _builder_version=”3.11″ header_font=”||||||||” body_font=”||||||||” result_message_font=”||||||||” custom_button=”on” button_text_size=”18px” button_border_width=”1px” button_font=”||||||||” button_icon=”%%72%%” button_icon_placement=”left” button_text_color_hover=”#005106″ button_bg_color_hover=”#ffffff” button_border_color_hover=”#ffffff” text_orientation=”center” /][/et_pb_column_inner][/et_pb_row_inner][/et_pb_column][et_pb_column type=”1_4″][et_pb_sidebar orientation=”right” area=”sidebar-1″ _builder_version=”3.11″ text_orientation=”center”]
[/et_pb_sidebar][et_pb_code admin_label=”Pixel – View Content” _builder_version=”3.11″]<script><!– [et_pb_line_break_holder] –> fbq(‘track’, ‘ViewContent’);<!– [et_pb_line_break_holder] –></script><!– [et_pb_line_break_holder] –>[/et_pb_code][/et_pb_column][/et_pb_section]